
Managed Security is an organization’s strategy that enables guaranteeing the security of its assets including all network traffic. It includes both software and hardware technologies. Access to the network is managed by effective managed security, which targets a wide range of threats and then arrests them from spreading or entering in the network.
It is also an integration of multiple layers of defenses in the network and at the network. Policies and controls are implemented by each managed security layer. Access to networks is gained by authorized users, whereas, malicious actors are indeed blocked from executing threats and exploits.
Our world has presently been transformed by digitization, resulting in changes in almost all our daily activities. It is essential for all organizations to protect their networks if they aim at delivering the services demanded by employees and customers. This eventually protects the reputation of your organization. With hackers increasing and becoming smarter day by day, the need to utilize managed security tool becomes more and more impotent.
SunFlex International Co., Ltd is experienced and provided the managed security solutions as below:
- Security Information and Event Management (SIEM)
- Privileged Access Management (PAM)
- Network Access Control (NAC)
- Data Loss Prevention (DLP)
- Application Security
- Endpoint Security
Security Information and Event Management(SIEM) products bring together all the information needed by your security staff in order to identify and respond to threats. These products are available in different forms, including virtual and physical appliances and server software.
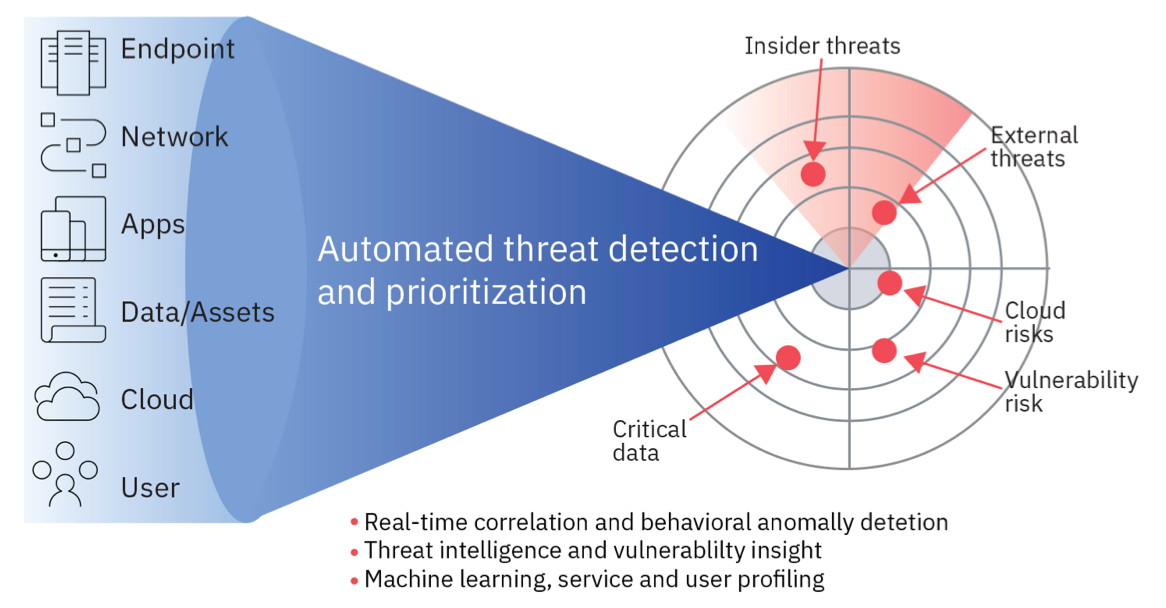
SunFlex takes this partnership with IBM to provide the SIEM solutions which is called IBM® QRadar® Security Information and Event Management (SIEM) to help security teams accurately detect and prioritize threats across the enterprise, and it provides intelligent insights that enable teams to respond quickly to reduce the impact of incidents. By consolidating log events and network flow data from thousands of devices, endpoints and applications distributed throughout your network, QRadar correlates all this different information and aggregates related events into single alerts to accelerates incident analysis and remediation. QRadar SIEM is available on premises and in a cloud environment.
Key Features
- Ingest vast amounts of data from on-prem and cloud sources
- Applies built-in analytics to accurately detect threats
- Correlate related activities to prioritize incidents
- Automatically parses and normalizes logs
- Threat intelligence and support for STIX/TAXII
- Integrates out-of-the-box with 450 solutions
- Flexible architecture can be deployed on-prem or on cloud
- Highly scalable, self-tuning and self-managing database
Automate security intelligence to rapidly detect threats
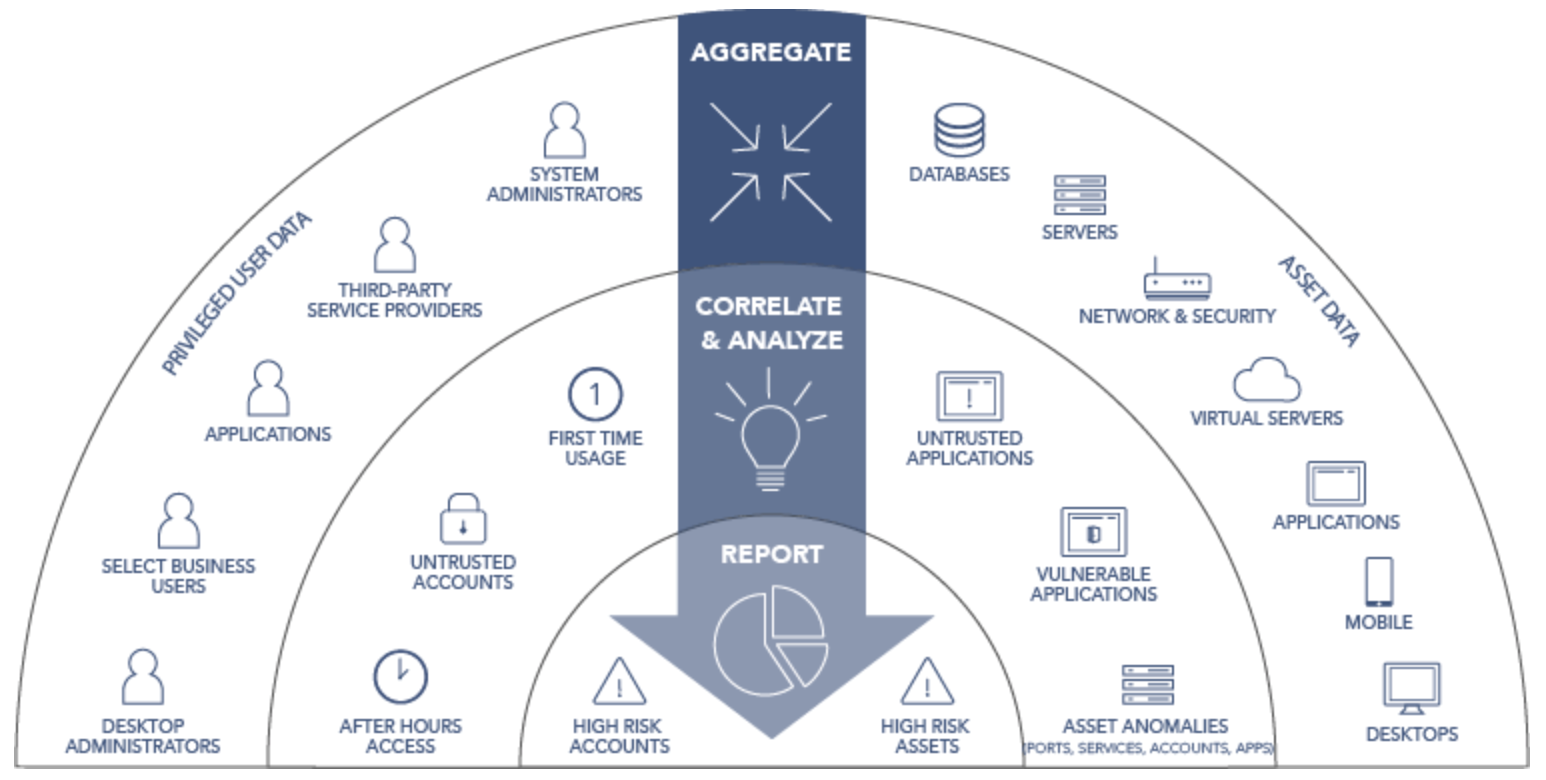
Privileged access management (PAM) consists of the cybersecurity strategies and technologies for exerting control over the elevated (“privileged”) access and permissions for users, accounts, processes, and systems across an IT environment. By dialing in the appropriate level of privileged access controls, PAM helps organizations condense their organization’s attack surface, and prevent, or at least mitigate, the damage arising from external attacks as well as from insider malfeasance or negligence.
While privilege management encompasses many strategies, a central goal is the enforcement of least privilege, defined as the restriction of access rights and permissions for users, accounts, applications, systems, devices (such as IoT) and computing processes to the absolute minimum necessary to perform routine, authorized activities.
SunFlex and BeyondTrust make this partnership to provide the best PAM solutions for FSI, MNC, TELCO sectors.
With us customer will benefits including:
- A condensed attack surface that protects against both internal and external threats: Limiting privileges for people, processes, and applications means the pathways and entrances for exploit are also diminished.
- Reduced malware infection and propagation: Many varieties of malware (such as SQL injections, which rely on lack of least privilege) need elevated privileges to install or execute. Removing excessive privileges, such as through least privilege enforcement across the enterprise, can prevent malware from gaining a foothold, or reduce its spread if it does.
- Enhanced operational performance: Restricting privileges to the minimal range of processes to perform an authorized activity reduces the chance of incompatibility issues between applications or systems, and helps reduce the risk of downtime.
- Easier to achieve and prove compliance: By curbing the privileged activities that can possibly be performed, privileged access management helps create a less complex, and thus, a more audit-friendly, environment.
Additionally, many compliance regulations (including HIPAA, PCI DSS, FDDC, Government Connect, FISMA, and SOX) require that organizations apply least privilege access policies to ensure proper data stewardship and systems security. For instance, the US federal government’s FDCC mandate states that federal employees must log in to PCs with standard user privileges.
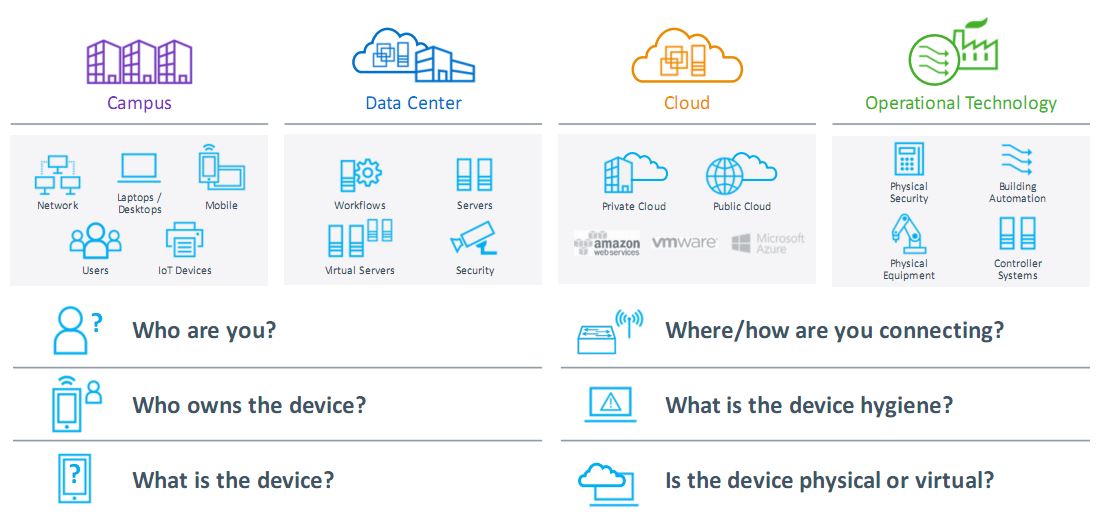
This network security process helps you to control who can access your network. It is essential to recognize each device and user in order to keep out potential attackers. This indeed will help you to enforce your security policies. Noncompliant endpoint devices can be given only limited access or just blocked. In this solution customer can also manage the integrated network asset which is called IT Asset Management.
With SunFlex, we are pleased to corporate with ForeScout to provide the NAC solutions.
The Forescout platform provides organizations with complete situational awareness of their extended enterprise and the ability to orchestrate actions to reduce cyber risk.
Forescout products deploy quickly with agentless, real-time discovery and classification of every IP-connected device for continuous posture assessment.
WHY FORESCOUT
- DISCOVER NON-DISRUPTIVELY: Ensure uninterrupted operations without device agents or active scanning, critical for IoT and OTdevices.
- ASSESS CONTINUOUSLY: Continuously monitor devices and enforce adaptive, granular policies that reduce operational and cyber risk.
- TAKE ACTION BOLDLY: Automate context-aware policies to increase security operations efficiency and free up skilled ITstaff.
- DEPLOY FLEXIBLY: See results fast using your existing physical and virtual network infrastructure and security tools.
- SCALE CONFIDENTLY: Monitor up to 2 million devices per deployment across campus, data center, cloud and OTnetworks.
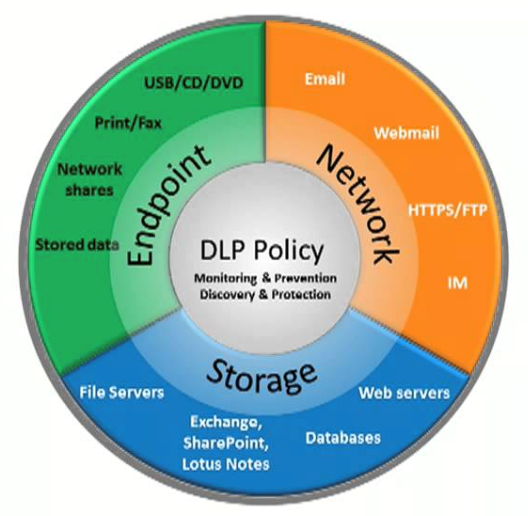
Organizations should guarantee that their staff does not send sensitive information outside the network. They should thus use DLP technologies, network security measures, that prevent people from uploading, forwarding, or even printing vital information in an unsafe manner.
SunFlex is proud to introduce Symantec Data Loss Prevention Solutions to drive total protection of your sensitive data which you will benefits:
- Stop data loss with the highest level of protection: Keeping information safe and compliant has
never been easy. But today, enterprises face new and unexpected security problems.
- Discover where data lives across every channel: cloud, email, web, endpoints, and storage
- Monitor how data is being used on and off the corporate network
- Protect data from being exposed or stolen in real-time
- Keep data safe while in use on endpoints : As employees become more mobile through the use of
laptops, company data becomes more vulnerable to data leaks and thefts – on and off the
corporate network. The Symantec DLP for Endpoint solution provides all the protection you need
to keep sensitive data safe and protected on endpoints. With Symantec DLP, a single lightweight
endpoint agent enables two modules:
- Symantec DLP Endpoint Discover scans local hard drives and gives you deep visibility into sensitive files that users are storing on their laptops and desktops. It provides a wide range of responses including local and remote file quarantining, and policy-based encryption and digital rights management enabled by the DLP Endpoint FlexResponse API.
- Symantec DLP Endpoint Prevent monitors users’ activities and gives you fine-grained control over a wide range of applications, devices and platforms. It provides a wide range of responses including identity-based encryption and digital rights for files transferred to USB. With Endpoint Prevent, you can alert users to incidents using on-screen popups or email notifications. Users can also override policies by providing a business justification or canceling the action (in the case of a false positive).
- Protect data in motion over the network The widespread adoption of collaboration tools and cloud
apps, coupled with risky employee behavior that companies may not even be aware of, increases
the risk of data exposure over business communications. The Symantec DLP for Network solution
monitors and prevents sensitive data from being leaked over a wide range of communication
protocols across your network.
- DLP Network Monitor captures and analyzes outbound traffic on your corporate network, and detects sensitive content and metadata over standard, non-standard and proprietary protocols.
- DLP Network Prevent for Email protects sensitive messages from being leaked or stolen by employees, contractors and partners. It monitors and analyzes all corporate email traffic, and optionally modifies, redirects, or blocks messages based on sensitive content or other message attributes.
- DLP Network Prevent for Web protects sensitive data from being leaked to the Web. It monitors and analyzes all corporate web traffic, and additionally removes sensitives HTML content or blocks requests. Network Prevent for Web is deployed at network egress points and integrate with your HTTP, HTTPS or FTP proxy server using ICAP.
- Protect data at rest across storage repositories Digital data is growing significantly, largely due to internally generated documents, yet few companies are focused on governing and protecting it. With Symantec DLP for storage, you can discover and secure sensitive data at rest—the data stored on file servers, endpoints, cloud storage, network file shares, databases, SharePoint and other share repositories.
- Protect data in the cloud Security concerns persist as companies continue to migrate legacy IT applications to public cloud services where it’s difficult to get the same level of visibility and control of sensitive data as on their own private servers. With Symantec’s DLP Cloud Services, you can extend powerful data protection controls to the cloud with the convenience of cloud-delivered DLP. They provide rich discovery, monitoring and protection capabilities for a wide range of cloud applications as well as on-premises applications.
- Manage from a single pane of glass As your data spreads across a wider range of devices and storage environments, the ability to consistently define and enforce policies becomes even more critical. Symantec DLP gives you a unified management console, the DLP Enforce Platform, which allows you to write policies once and then enforce them everywhere – across all data loss channels.
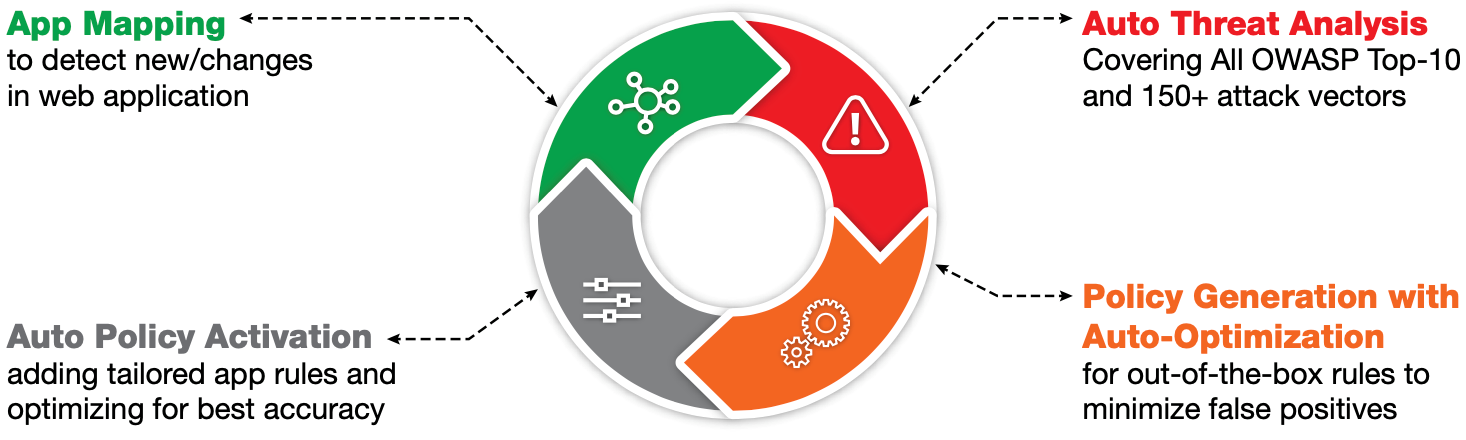
It is important to have an application security since no app is created perfectly. It is possible for any application to comprise of vulnerabilities, or holes, that are used by attackers to enter your network. Application security thus encompasses the software, hardware, and processes you select for closing those holes. SunFlex International works closely with top WAF vendors to provide the solutions to benefit customer as below:
- Advanced Web Application Security
- Comprehensive and Accurate Security Coverage
- Automated Protection from Zero-Day Web Attacks
- Leveraging Machine-Learning Algorithms for Auto Policy Generation
- Continuous Security Delivery
- IP-agnostic Device Fingerprinting for Bot Protection
- Unique Out-of-Path Deployment with Full, Line-Speed Mitigation
- All-in-One Application Delivery & Security
- Fully Managed Web Application Protection
Endpoint Security, also known Network Protection is a methodology used for protecting corporate networks when accessed through remote devices such as laptops or several other wireless devices and mobile devices. The Endpoint Protection software presents seven layers of defense that include viruscope, file reputation, auto-sandbox, host intrusion prevention, web URL filtering, firewall, and antivirus software. All this is offered under a single offering in order to protect them from both unknown and known threats.
Penetration Testing is the most efficient way to accurately identify security vulnerabilities. It is a method used to evaluate the security of a network, web application, web service, and any other software system or device by using the techniques a hacker would use in a safe and controlled manner.

- Information Gathering SunFlex experts work with the customer to clearly define and document test objectives, scope and rules of engagement. We conduct one or more interviews to gain a thorough understanding of the customer’s testing goals and needs, security and compliance requirements, business risks and other related factors.
- PLANNING ANALYSIS
Analyze Information gathered from the above phase Our Security Experts Identify specific type of security tests applicable for applications and also Understand business logic involved in the application and Determining possible attack scenarios
The SunFlex team collects and examines key information about the specified target and its infrastructure. Depending on the scope of testing, the information may include functionality, use cases, user roles, architecture, security mechanisms, security-critical areas, hosting environment, and more. This information helps develop a testing plan and identify possible attack patterns on the chosen application or network to properly target automated scanning software, and to fine tune the manual testing process.
- VULNERABILITY DETECTION Analyze Information gathered from the above phase Our Security Experts Identify specific type of security tests applicable for applications and also Understand business logic involved in the application and Determining possible attack scenarios
- PENETRATION TESTING SunFlex experts work with the customer to clearly define and document test objectives, scope and rules of engagement. We conduct one or more interviews to gain a thorough understanding of the customer’s testing goals and needs, security and compliance requirements, business risks and other related factors.
- REPORTING After completion of penetration tests detailed reports are prepared for taking corrective actions. All identified vulnerabilities and recommended corrective methods are listed in these reports. You can customize vulnerability report format (HTML, XML, MS Word or PDF) as per your organization needs.








